Tag: Strategy
Cyber (In)Securities – Issue 162 – Snapshot Edition
16 Billion Passwords Leaked, Qantas Targeted, and Active Exploits Disclosed This edition covers a string of major cybersecurity developments shaking industries worldwide. A silent breach has exposed 16 billion passwords, triggering government advisories. Qantas confirmed it was contacted by a potential cybercriminal following a data …
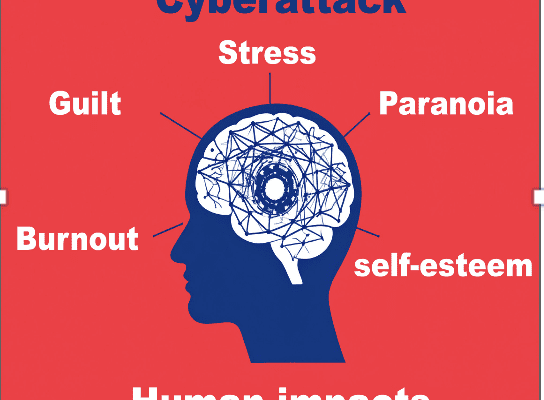
What happens to Heroes?” EPISODE #8: The Unsung Heroes of the digital world by Didier Annet
The Psychological Impacts of Cyberattacks What I will call the “Heroes” The psychological impacts hitting the Heroes. “Yes, I’m different today. Insecurity is much more prevalent for me, it’s much more present in my head and in my everyday life. I try to make people …
Cyber (In)Securities – Issue 161 – Snapshot Edition
Cyber (In)Securities – Edition 161: Qantas Data Breach, AI-Powered Phishing, and Global Cybersecurity Shifts In this week’s Cyber (In)Securities, we spotlight the Qantas Frequent Flyer breach that affected over six million users. While financial data may not have been exposed, the compromise of travel patterns, …
Transformation in Technology and Cybersecurity by Sapann Harish Talwar
In today’s increasingly digital and hyperconnected world, transformation in technology and cybersecurity is no longer a choice. It has become a strategic imperative. Organizations across all industries are accelerating efforts to digitize their operations, modernize infrastructure, and adopt emerging technologies such as cloud computing, artificial …
Cyber (In)Securities – Issue 159 – Snapshot Edition
(In)Securities | Edition 159: ICS Alerts, IntelBroker Fallout, and Cybercrime Crackdowns This edition covers rising threats to critical infrastructure, major vulnerability disclosures, and global law enforcement action. CISA has released new Industrial Control Systems advisories and expanded its Known Exploited Vulnerabilities catalog. Meanwhile, the arrest …
AI Security Challenge
The landscape of AI security presents a unique challenges. Adversaries are increasingly sophisticated, aiming to manipulate AI models, exfiltrate sensitive data, or exploit vulnerabilities within AI systems for various malicious ends. On top they are using /consuming millions of feeds , so we are looking …
Not Just European, But Trustworthy: What DNS4EU Reminds Us About Sovereignty, Surveillance, and (Actual) Security
When Infrastructure Becomes Political Once upon a time, infrastructure was invisible. It quietly kept the world running – roads, pipes, power grids, protocols. You only noticed it when it broke. But digital infrastructure isn’t invisible anymore. It’s political. It’s strategic. And increasingly, it’s personal. In …
03:17 AM: When Everything Goes Wrong by Jonathan Wood
There is a very specific time of day when it all seems to fall apart. For Cyber Security, that time is around 03:17 AM. If you’re in security, you will recognise this feeling, the kind of sensation where you feel there is an elephant in …
Cyber (In)Securities – Issue 158 – Snapshot Edition
(In)Securities | Edition 158: Internet Users Advised to Change Passwords After 16bn Logins Exposed This edition dives into the massive RockYou2024 data dump, critical Citrix NetScaler flaws, and global breaches spanning Canada, Iran, and South Africa. We track MFA bypasses used by Russian hackers, malware …