The Human Factor in OT Security Incidents: Understanding Insider Threats and Social Engineering in Critical Infrastructure by Rupesh Shirke

Introduction
The human factor is an essential but overlooked security component in Operational Technology (OT) systems within critical infrastructure. However, although many technological defenses have improved, insider threats and social engineering remain serious due to inherent human activity and organizational culture vulnerabilities. Operators of OT usually lack specialized cybersecurity expertise, which makes them even more susceptible to exploitation by, say, spear phishing, baiting, and pretexting (Hammoudeh, 2018). Insider threats are particularly challenging because they are authorized personnel who abuse their legitimate access maliciously or inadvertently, evading most traditional security controls. This dual nature of threat actors demands an appreciation that is nuanced and goes beyond purely technical solutions. Social engineering takes advantage of trust and cognitive biases via psychological manipulation, making it an effective attack technique for those trying to breach critical infrastructure sectors where continuity of operations is paramount. The seminal events showcasing the apocalyptic consequences when human factors are ignored; the case studies illustrate how awareness and procedural compliance shortfalls can facilitate breaches with far-reaching implications. Hence, effective mitigation solutions must comprise comprehensive risk management frameworks emphasizing personnel training, behavioral monitoring, and cultivating a security-conscious organizational culture (Ghafir, 2018). By examining insider threats and social engineering attacks in OT systems in-depth, this essay aims to demystify the complex interplay between human vulnerabilities and cybersecurity challenges in critical infrastructure domains. These dynamics must be understood to build resilient defenses that can respond to technological vulnerabilities and the underlying human factors behind security breaches.
Defining Insider Threats in OT Security:
Insider threats to Operational Technology (OT) security are an underrecognized and serious risk vector in critical infrastructure environments. Unlike external cyberattacks, insider threats originate from individuals with authorized access to OT systems, including employees, contractors, or trusted partners. These insiders can misuse their authorized permissions maliciously or inadvertently and, in doing so, create potentially significant disruptions to industrial control systems (ICS), which regulate critical services such as energy production, water treatment, and transportation networks. Placing insider threats in the context of OT security demands understanding the distinctives of OT environments and the intricacy of insider activity.
OT networks are, by definition, different from legacy IT infrastructures due to their real-time operational requirements, heritage, and safety-critical uses. Insider threats in the OT arena do not just equate to intellectual property theft or data theft but to physical injury and endangering human life. Thus, an insider threat to OT security is any action by a trusted person that breaks the confidentiality, integrity, or availability of OT assets, either through sabotage, espionage, carelessness, or mistake. This broad definition encompasses intentional acts such as modifying control logic or unauthorized system parameter modifications and accidental actions such as misconfiguration through inadequate training.
In addition, the motivation behind insider threats in OT systems is two-faced and highly complicated. They might be for money and ideology, or sheer negligence due to improper awareness of cybersecurity threats. The trick lies in distinguishing between malicious attacks and accidental compromises, since both can potentially generate similar disastrous effects on critical infrastructure resilience. Understanding these nuances is paramount to creating effective detection mechanisms that are OT-specific because traditional IT-oriented approaches may not work in OT environments.
Defining insider threats in OT security means understanding the special operational context and the reality that trusted personnel pose a significant threat by malicious intent and inadvertent error. This kind of comprehensive strategy is needed to address human factors that compromise the security stance of critical industrial systems.
Social Engineering: Tactics And Techniques:
Social engineering in the context of Operational Technology (OT) security exploits human nature to manipulate individuals into divulging confidential information or activities that compromise the integrity of the systems. Unlike technical attacks, which target software weaknesses, social engineering leverages trust, fear, urgency, or authority to bypass traditional security mechanisms. Some standard techniques utilized are phishing, pretexting, baiting, and tailgating, each aiming at specific human behaviors in critical infrastructure networks.
Phishing remains one of the most prevalent methods used on OT personnel. Fraudulent emails or messages crafted to appear legitimate are created by attackers to get recipients to click on malicious links or reveal sensitive credentials. These messages are more successful when spoofing trusted sources such as vendors or internal departments. Pretexting involves establishing a scenario to gain unauthorized access; for example, an attacker may pretend to be a maintenance employee who needs access to a system under pretenses. Baiting exploits curiosity by offering something desirable—e.g., free software or USB drives—that contain malware targeted at OT networks when accessed.
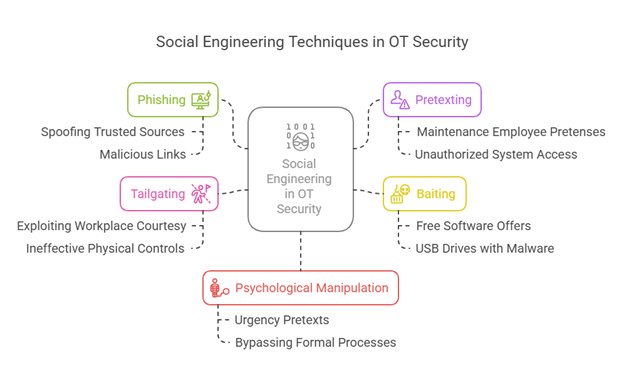
Tailgating is a physical social engineering attack where an unauthorized individual follows an authorized employee into secure areas without credentials. It exploits common workplace courtesy and illustrates the ineffectiveness of physical security controls in critical infrastructure facilities. Further, psychological manipulation through pressure, such as creating a pretext of urgency, can bully insiders into bypassing formal processes.
The effectiveness of such methods is amplified in OT environments due to the complexity and usually decentralized ICS networks, where personnel may prioritize operational continuity over strict adherence to cybersecurity protocols. Moreover, insufficient cybersecurity training and awareness for non-IT staff further enhance susceptibility to social engineering attacks. It is essential to understand these diverse techniques so that overall defense mechanisms can be developed according to the particular concerns for OT industries. By understanding how attackers are exploiting human factors through social engineering, organizations can prepare against potential attack vectors and implement targeted training programs along with technical controls to mitigate insider threats successfully.
Case Studies of Notable Incidents:
One of the most iconic examples of an insider threat in OT security is the Ukrainian power grid attack in 2015. It was a collaborative cyberattack that caused mass disruption of the power supply to hundreds of thousands of residents. The investigation revealed that attackers employed social engineering tactics to gain network access, with spear-phishing emails sent to employees in the utility company. The success of this attack illustrates how human factors, like vulnerability to deceptive communication and poor employee training, can be exploited to weaken critical infrastructure. Additionally, from within, attackers employed legitimate credentials and tools, highlighting the role that insiders or compromised insiders can play in enabling widespread damage.
Another significant case is the 2017 Triton malware attack on a petrochemical facility’s safety instrumented system (SIS). While at first attributed to external threat actors, subsequent reports had suggested potential insider involvement or, at the minimum, the exploitation of insider familiarity with operational technology processes and safety systems. This attack served to underscore the unique threat posed by insiders with deep technical familiarity with OT environments to circumvent traditional security controls and disrupt safety mechanisms key to preventing catastrophic failures.
The 2020 Oldsmar water treatment facility hack also shows insider-related vulnerabilities compounded by social engineering methods. Remote access was achieved via compromised credentials and a bid to manage chemical levels in water systems. Despite no physical harm from prompt action, the attack demonstrated how weak authentication protocols and insufficient monitoring, often related to human error or lack of alertness, can be exploited by attackers to reach vital systems.
These cases show that insider threats in OT environments are not merely a function of malicious intent but also encompass unintentional behavior facilitated by social engineering exploits. They reveal systemic vulnerabilities such as weak employee awareness programs, weak segregation of duties, and lack of effective anomaly detection specific to OT environments. Learning about these incidents gives important insight into how human factors overlap with technological vulnerabilities and calls for in-depth strategies combining behavioral analysis with technical defenses to secure critical infrastructure against emerging threats.
Mitigation Strategies For Insider Risks:
Insider threat mitigation in operational technology (OT) environments must include a multifaceted approach that combines technical controls, organizational policy, and human-related measures. Successful mitigation depends ultimately on the use of strong access control mechanisms. Role-based access control (RBAC) makes it possible to give employees just the minimum necessary privileges to do their work to minimize the avenues for malicious or accidental misuse of key systems. Besides that, ongoing surveillance through anomaly detection systems can identify unusual user behavior characteristic of insider threats to intervene before severe damage is done.
No less important is creating a security-minded organizational culture. Regular training sessions specific to OT personnel must emphasize the particular risk and consequences of insider threats within critical infrastructure contexts. These educational efforts must move beyond general awareness of cybersecurity topics to encompass scenario-based training reflective of real social engineering tactics and potential insider motives. Developing a culture where employees feel comfortable reporting suspicious activity without fear of retribution also enhances early detection.
From a regulatory perspective, conducting extensive background checks at recruitment helps to sift for potential risk factors from insiders. In addition, applying explicit rules of discipline and enforcing segregation of duties dissuades adverse behavior by elevating responsibility and reducing opportunities for collusion or misbehavior. Automated audits and reviews of user access further support efforts by enforcing conformance with intended protocols.
Technical controls such as encryption and data loss prevention (DLP) software reduce the insider threat risk of insiders attempting to exfiltrate sensitive information. Including endpoint detection and response (EDR) solutions in OT networks allows for the rapid detection and containment of insider-induced anomalies.
Overall, insider risk mitigation in OT security needs to be a cohesive strategy of rigorous access controls, continuous behavioral monitoring, human factors training of staff, rigorous personnel vetting procedures, authoritative policy enforcement, and advanced technological defenses. Only by using this comprehensive framework can firms adequately address the complex threat that insiders pose to safeguarding critical infrastructure assets.
Conclusion:
The discussion of “The Human Factor In OT Security Incidents: Understanding Insider Threats and Social Engineering In Critical Infrastructure” highlights the complexity and absolute priority that needs to be given to managing human vulnerabilities in operational technology networks. By delineating insider threats as they pertain to OT security, the paper describes how individuals with privileged access can inadvertently or intentionally compromise systems fundamental to national infrastructure. The study of social engineering tactics also emphasizes that technical defenses are insufficient; attackers commonly exploit mental manipulation to bypass sound security measures. The case studies herein are compelling pointers to real-world effects when human factors are neglected, indicating the scale and severity of incidents that have disrupted essential services. These case illustrations reinforce the argument that understanding attacker motivations and methods is central to developing effective countermeasures.
Furthermore, the discussion of mitigation strategies provides a helpful guide for organizations seeking to enhance their defenses against insider threats, advocating a combination of technological defenses, employee training, behavioral monitoring, and organizational policies tuned to the unique requirements of OT networks. Overall, this review illustrates that critical infrastructure security needs to be addressed holistically, with human factors being given as much consideration as technical controls. Future research must keep evolving adaptive countermeasures that thwart social engineering techniques and insider behavior amidst increasingly interconnected OT systems. Lastly, boosting human-centered security practices is vital to minimizing vulnerabilities and ensuring the security and trustworthiness of critical operational technologies during a time of increasing cyber threats.
References
Ghafir, I. (2018). Security threats to critical infrastructure: the human factor. https://link.springer.com/article/10.1007/s11227-018-2337-2.
Saleem, J. (2025). The Human Factor in Cybersecurity Events: Critical Education …. https://domesticpreparedness.com/articles/the-human-factor-in-cybersecurity-events-critical-education-components.
Hammoudeh, M., (2017). (PDF) Security threats to critical infrastructure: the human factor. https://www.academia.edu/43047571/Security_threats_to_critical_infrastructure_the_human_factor.
Faour, H. (2025). [PDF] HUMAN FACTORS IN CYBERSECURITY: RISKS AND IMPACTS.
https://www.securityscience.edu.rs/index.php/journal-security-science/article/download/54/34/.
Prenosil, V., (2009). Human factors in information security: The insider threat – Who can https://www.sciencedirect.com/science/article/abs/pii/S1363412710000051.
About the Author:
Rupesh Shirke, CISSP works at the forefront of Critical Infrastructure Protection and ICS/OT Cybersecurity.
He is a mentor, speaker, writer, global advisor, and volunteer, consistently driving resilient solutions for a secure future.