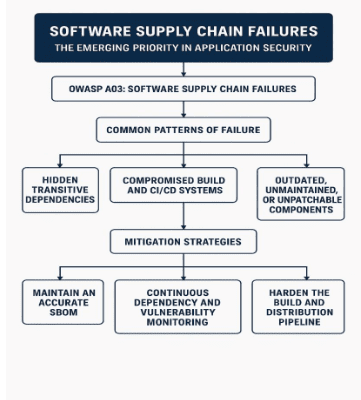
Software Supply Chain Failures: The Emerging Priority in Application Security by Karthikeyan Ramdass
As modern software ecosystems become increasingly interconnected, software supply chain security has emerged as one of the most critical challenges in application security today. In this article, CyAN member Karthikeyan Ramdass examines why Software Supply Chain Failures, ranked as A03 in the OWASP Top 10:2025, …