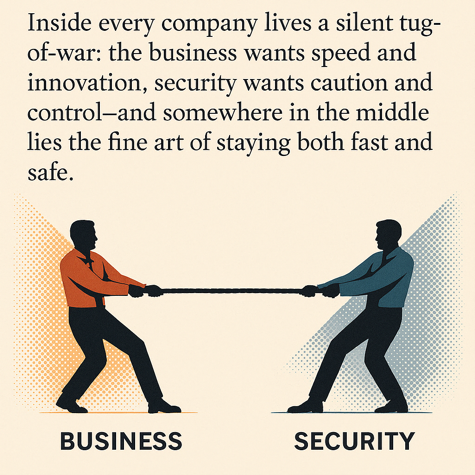
“What happens to Heroes?” EPISODE #7: The Unsung Heroes of the digital world “
The Psychological Impacts of Cyberattacks What I will call the “Heroes” Excerpts from Interviews with Heroes THINGS TO REMEMBER About the Author Didier Annet is an Operational & Data Resilience Specialist and a Certified Professional Coach dedicated to empowering individuals and teams to navigate the …