Behind the Posts: How I Identify My Top 10 Cyber Threat Groups Each Week by Dan Elliott

How I separate noise from real risk…
I’ve been asked numerous times how I select the threat groups I write about – why one and not another. So, I thought I’d take a perfectly good Sunday afternoon to share.
MITRE currently tracks at least 133 cyber threat groups and Microsoft more than 1,500. Much like a hydra, as law enforcement closes in on a few group members, the others seem to splinter into new factions. With new groups continuing to appear, how does one separate the noise from real risks to their organisation?
Each week, I publish a #WeekendReading carousel highlighting a cyber threat group that I think CISOs and executives should be aware of in order to stay ahead of the curve. Behind the scenes, I track and rank my top 20 active threat groups. It’s not perfect, but it’s not just gut instinct or what makes news headlines. Behind every ranking is a structured, intelligence-based framework where I evaluate impact, recency, and the evolving threat landscape.
Why is this relevant to you?
If you follow me, you deserve to know why I post these groups.
And if you’re a CISO, a business leader, or a Board member, you know that the challenge isn’t getting information, it’s getting the right information in a timely and succinct format.
Here’s how I build my weekly rankings and what it means for businesses managing cyber risk.
A structured approach: The 10 domains I chart
Cyber threats aren’t all equal. Some groups are highly active, targeting critical industries, while others have faded into the background or landed behind bars. I evaluate each group across 10 weighted domains, with a set of category questions under each, ensuring a balance between data-driven intelligence and my experienced analysis.
I score each question for each domain from 1 to 10, where:
- 1-2: Minimal activity or impact
- 3-4: Occasional or limited operations
- 5-6: Moderate, sustained activity
- 7-8: Frequent, high-profile attacks
- 9-10: Persistent, high-impact, and evolving operations
The result? A clear, ranked list that I use to prioritise relevant and dangerous threat groups for the current week.
Beyond data: Intelligence and context
While structured data plays a key role, not everything is quantitative in cyber intelligence. Groups often operate discreetly or with support of government, and publicly available data can be incomplete, misleading, or downright inaccurate. That’s why I consider:
- Expert insights from industry reports, whitepapers, and real-world breach analysis.
- Conversations with peers across intelligence, risk, and cybersecurity circles.
- Patterns from historical activity, filling in gaps where data might be lacking.
A blend of data, intelligence, and experience ensures a more accurate assessment – rather than relying on surface-level reports and headlines.
Example: Why Stone Panda (APT10) ranked #3 for me this week
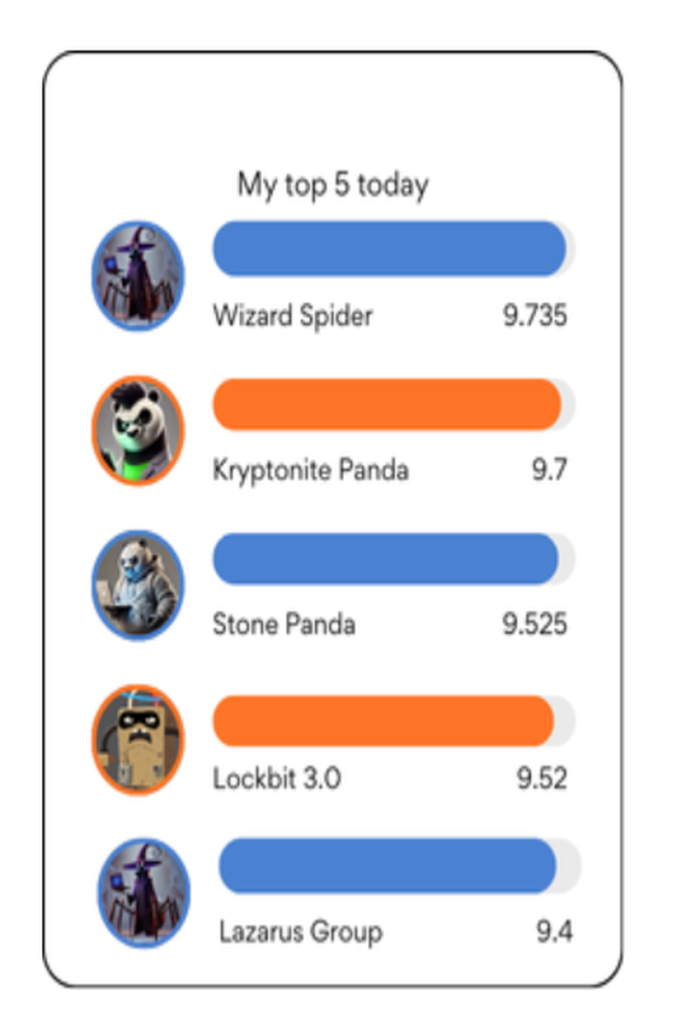
One of the most active and persistent threat groups, Stone Panda (APT10) has been consistently targeting organisations across ANZ and globally. Here’s how they scored in my latest ranking:
- Recency of Activity: 8.5 – Multiple reports indicate recent operations targeting managed service providers (MSPs) and supply chains.
- Frequency of Attacks: 8.4 – A steady stream of attacks, including espionage-focused breaches in finance, healthcare, and technology.
- Geographical Impact (ANZ): 9.0 – High-level targeting of ANZ-based enterprises, particularly in critical sectors (although threats are global, trends move across 3-4 regions).
- TTPs (Techniques, Tactics, Procedures): 9.3 – Use of sophisticated custom malware, supply chain infiltration, and long-term persistence techniques.
- Industries at Risk: 9.1 – Focused on a wide array of industry sectors with valuable IP, including technology, healthcare, and government (showed variability).
- Financial & Operational Impact: 8.6 – Based on available information, breaches linked to APT10 have led to significant financial losses and business disruption.
- Exploitation Methods: 8.7 – Effective use of zero-day vulnerabilities, credential theft, and lateral movement techniques.
- Global Collaboration: 7.9 – Evidence of ties to other advanced groups and intelligence-sharing mechanisms (based on scripts used and conversation).
- Visibility (Public Claims): 7.8 – While not as overt as some ransomware groups, APT10’s activities frequently surface in intelligence reports, tracking sites, and media, noting a willingness to be seen conducting these activities.
- Law Enforcement Pressure: 7.9 – Sanctions and attribution from global law enforcement, but no major operational takedowns demonstrate to me a talent for both remaining hidden and active simultaneously.
What this means for CISOs & Executives
This group’s ranking isn’t just based on a few past attacks or news reports – it reflects an ongoing active threat. For CISOs, CEOs, and Board members, when you see me post about a group, you can be sure my approach focuses on a structured way to assess real threats, rather than reacting to the loudest headlines.
Key takeaways:
- Focus on real risks impacting your industry and geography.
- Structured methodologies help cut through noise and prioritise security spending.
- Cyber risk isn’t static – neither should your threat intelligence be.
The broader picture and what this isn’t
The “Weekend Reading” posts began as a hobby to keep myself informed after leaving the intelligence community and an opportunity to share with peers and clients so they could benefit from my ongoing research.
There are now roughly 1,000 of you who view the weekly carousel.
These briefs should not replace your own cyber threat intelligence, and they are drawn from my own resources and not Zurich information (which we use with clients for other services).
But by the same token, I want you to be confident that what I provide will add value for you.
If you want to know how these cyber threats impact your specific industry, or how to build intelligence-driven risk management strategies, let’s connect.
What’s your take? How do you prioritise cyber threats in your organisation?
Drop a comment below. 👇
About the Author
Dan Elliott
📌 LinkedIn Profile
Dan is a Global Cyber Security Advisor, Former Intelligence Officer, and International Keynote Speaker. He specializes in cyber resilience strategy, intelligence analysis, and threat research, helping organizations navigate complex security landscapes.
🔗 Read Dan’s original LinkedIn post on identifying top cyber threat groups