The following is a translation by James Briscoe, CyAN Secretary General. The original Japanese announcement by Fujitsu details the results of an investigation by Fujitsu into unauthorised external communications on one of their services.
This announcement has not yet made it into the English language.
Please find the original Japanese announcement on Fujitsu’s site here.
Unauthorised communications from network equipment relating to FENICS internet services (survey results)
20 Feb 2023.
Fujitsu Limited.
We made a public announcement on 23 December 2022 regarding unauthorised external communications on our FENICS Internet service, and we would like to report on the results of an investigation that was subsequently carried out to capture the full picture of this incident.
We would like to express our deepest apologies to all concerned for the great concern and inconvenience this has caused.
We take this incident very seriously and will further strengthen our security measures to ensure that our customers can use our services with peace of mind.
1. Investigation Results
On 9 December, we confirmed an incident in which unauthorised communications were being transmitted externally from some of the network equipment comprising the FENICS internet service.
As a result of this investigation, FENICS has identified the network equipment that was technically capable of unauthorised external communications and determined the scope of the impact of this incident.
- Overview of the incident
It was found that the communication information passing through the network equipment during the time of the unauthorised communication was in a state where it was technically possible to steal it from the outside.
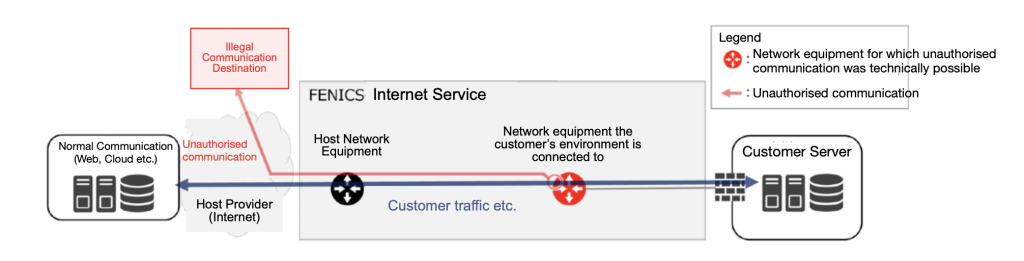
(2) Infringement traces identified by the investigation
In this investigation, in order to identify the scope of the impact and the cause of the incident, we conducted a digital forensic investigation of the network equipment, server equipment, and service operator PCs comprising the FENICS service in their entirety, and of the network equipment and service operator PCs that were known to have been illegally communicating and that could have been compromised, in order to gain an overall picture of the incident. A digital forensic investigation was conducted to gain an overall picture of this incident. The details uncovered as a result are as follows:
- A program was found to be operating on some network devices to steal the account information (username/password) of service operators who had logged into the devices. As a result of the investigation, it was found that the specific service operator accounts that had been stolen were being misused in this incident.
- It was found that the network equipment on which the unauthorised communication took place had a function to bypass authentication to the equipment and a function to stop log output.
- No traces of suspicious infringement were found on the server equipment or the service operator’s PC.
(3) Scope of impact of this incident
Using the identified infringement traces as clues, the entire equipment comprising the FENICS service was investigated and the network equipment that was technically capable of unauthorised external communication was identified. The period during which it was technically possible to steal communication information from the outside was also identified, based on when the unauthorised functions were incorporated.
Based on the network devices and periods identified, we have determined which customers using FENICS services and other company services were communicating during the period in question with communications that could technically be stolen externally, and we will be reporting on this in due course.
2. Causes of the Incident and Actions Taken
It was found that the external access control settings of some network equipment were not appropriate and that the network equipment itself was not blocking communications to the Internet.
(1) Unauthorised communication blocking
- Corrected and strengthened restrictions on communications from the Internet to the network devices themselves.
- Blocking communications from the network equipment itself to the Internet.
(2) Enhanced monitoring
- Monitoring of unauthorised access from the Internet to the network equipment itself has been strengthened.
- Monitor communications to the Internet from the network equipment itself.
(3) Reset usernames/passwords for service operator accounts
(4) Replace network equipment that has been found to be communicating illegally
3. Future Measures
In light of this incident, further security enhancements and measures to prevent recurrence are being considered to strengthen and maintain the security of FENICS services, including the following:
(1) Further security enhancements (target end of March):
- A system for analysing communication flows and detecting suspicious traffic at an early stage.
- A mechanism to detect suspicious behaviour in network and server equipment.
(2) Measures to prevent recurrence (plan formulated by the end of March):
- Reinforcement of security control functions to ensure security and continuous improvement.
- Review and unification of security operation rules and policies.
- Periodic verification of the effectiveness of security measures using diagnostic tools.
Fin.
Questions from Customers
Q. Why did Fujitsu announce these details at this time?
A. We conducted an investigation to gain an overall picture of the incident by the end of January. Now that the investigation has been completed, we have published this notice to ensure that all customers using our service are aware of the situation. Customers who were not affected at the time of the announcement on 23rd December 2022, but were confirmed to be potentially affected by the investigation, are also being contacted. As a future plan, we aim to formulate a recurrence prevention plan by the end of March and report back to you.
Q. Is there any unauthorised access inside services provided by Fujitsu, such as FJcloud-O?
A. Other than the information security event confirmed for the FENICS Internet service, no information security events have been confirmed for FJcloud-O, etc. No information security events have occurred within FJcloud-O or other services used by customers.
Q. Our company uses another Fujitsu service (we are considering introducing the service), but we would like to confirm this matter. How can we do this?
A. If there is a Fujitsu representative in charge of the customer, please contact the person in charge. If you do not have a Fujitsu contact person, please contact the Fujitsu Contact Line.

