The CyAN Blog
Cybersecurity Advisors Network’s blog is a forum for CyAN members and friends to present their work and analysis to the broader information security community.
Introducing the mentors of the CyAN Global Mentorship Programme | March–May 2026
We are proud to welcome an outstanding group of mentors who will be supporting the March 2026 intake of the CyAN Global Mentorship Programme. This mentor cohort represents deep, real-world experience across cybersecurity, privacy, risk, governance, law, artificial intelligence, and trust and safety. Based across …
Beyond Compliance: Building Continuous Confidence in Risk, Governance, and Cybersecurity by Pathan Humam
Across industries, organizations are investing heavily in cybersecurity controls, compliance frameworks, and assurance programs. Yet many leadership teams still struggle to answer a simple but critical question with confidence: “What is our risk posture right now—and can we trust it?” As cyber threats accelerate, regulatory …
Real Estate’s Data Reckoning Was Always Coming
In September 2024, I published an article on LinkedIn titled The Cost of Convenience: How Data Mismanagement and Ticket-Clipping Models are Failing Renters. It was written out of growing unease, not hindsight. At the time, the concern was simple but deeply uncomfortable: real estate agencies …
When “Just a Tool” Stops Being a Defence
Over the past three days, a pattern has emerged that is difficult to dismiss as coincidence, mischief, or edge-case misuse. Investigations reported by reputable outlets, including The Guardian, reveal that Grok, an AI image generation tool, has been used to produce sexualised fake images of …
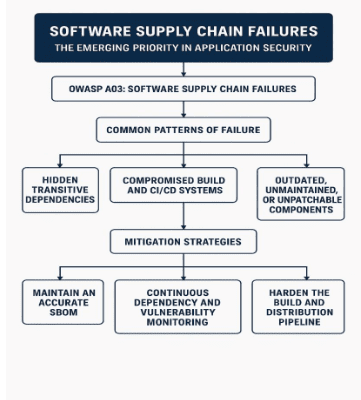
Software Supply Chain Failures: The Emerging Priority in Application Security by Karthikeyan Ramdass
As modern software ecosystems become increasingly interconnected, software supply chain security has emerged as one of the most critical challenges in application security today. In this article, CyAN member Karthikeyan Ramdass examines why Software Supply Chain Failures, ranked as A03 in the OWASP Top 10:2025, …
Navigating EU Compliance for AI-Enabled Wearable Medical Devices: MDR, AI Act, GDPR and Data Act Interplay
You can download this edition by clicking the three dots icon on the far right and selecting Download PDF File. For the best reading experience, we recommend enlarging it by clicking the fullscreen icon, which is the third icon from the right. All article titles …
Reflections on Day Two of the 2025 Neurotechnology Summit: Capability, Governance and the Questions We Must Answer
If Day One explored what neurotechnology means for individual minds, Day Two confronted what it will mean for societies, states and the systems that govern them. The conversations shifted from personal rights, clinical ethics and emerging applications to national capability, infrastructure, defence, public policy and …