From Targets to Co-Designers: Empowering Gen Z in the Age of AI
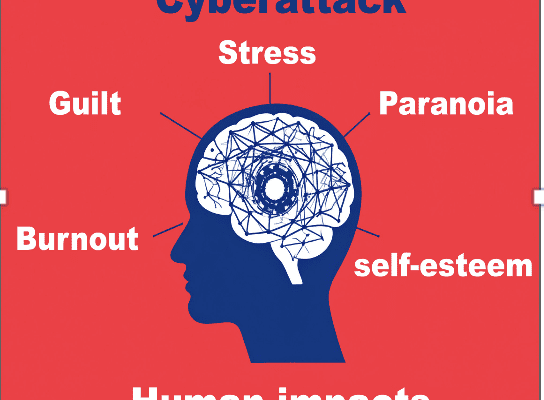
Gen Z is the first generation to grow up entirely within an AI-powered world. From school apps that track their attention spans to platforms that curate their every scroll, they’ve been nudged, measured, and profiled by algorithms long before most could give meaningful consent. And …