What happens to Heroes?” EPISODE #4: The Unsung Heroes of the Digital World by Didier Annet
The Psychological Impacts of Cyberattacks
This is the fourth episode of a story related to individuals who, in a matter of moments, transition from “employees” to “rescuers” in the immediate aftermath of a destructive cyberattack.
What I will call the “Heroes”!
Let’s Rewrite the Story of a Cyberattack – Uchrony of a losing scenario
“The problem is that sometimes operations and security don’t go together. You have to serve the business first, which is what makes the company make money. Our mission is to make operations and production work. But on top of that come the security requests. The issue is that we didn’t have the substance or the importance of what this was going to bring us. We know it’s important, but day-to-day activities take precedence..”
Excerpt From the Interview
My book is dedicated to encouraging companies to consider the human aspect in the context of cyber attacks. But coaching has only been part of my professional practice for the past 4 years. For over 25 years now, my career has been centered on helping customers strengthen their data resilience. This scenario is freely inspired by one of my corporate clients …
Typical identification factor: “It only happens to others!”
Once upon a time, there was a company with an exacerbated DNA of self-confidence, where all the energy was devoted to more business, faster, and where the only valuable thing was to say yes to business. Yes at all cost. Moreover, anyone who says no or tries to make sense is eliminated by the organization’s dynamics.
This scenario presents a lose-lose situation for the company. Despite recognizing, at the conscious level, the importance of IT security and attempting to implement a resilience strategy, the resources allotted are insufficient. The initiatives are never completed. Led by its instinct, the company prioritizes business over cybersecurity, creating a paradoxical corporate stance on cybersecurity.
This mindset frustrates those responsible for cyber resilience and embeds the notion that security measures are “costly and time consuming,” inevitably leading to internal conflicts and stress.
A losing scenario is marked by frustration among teams and between management levels due to inconsistencies between stated policies and actual practices. This creates ongoing tension around cybersecurity. Although the IT infrastructure may be effective and efficient, the company’s economic success relies on daily operations with the resources allocated at all costs to serve the client (business first). Thus, the level of cyber resilience ultimately depends on the technical staff’s motivation. Some individuals may prioritize the protection of IT systems over their own well-being and relationships, creating an unhealthy work-life balance that would need rectification.
In the face of an attack, the team’s advanced technical skills will allow for a prompt and effective response. Incident management procedures exist and are generally followed, ensuring a technologically sound reaction. However, underinvestment leads to gaps in the standard protection sequence (identification, protection, detection, response and recovery), which exacerbates both the technical and human impacts. These can range from complete system contamination to data theft and destruction.
To make up for these shortcomings, certain people may choose to become heroes, taking on additional duties and frequently going above and beyond. In contrast, others may hide their previous negligence, further exacerbating the crisis. This dynamic can happen intentionally or unintentionally.
Despite having a response strategy, these disruptions can hinder communication and objective evaluation, resulting in disputes and blunders during the rehabilitation phase.
The more significant the setbacks, the more the need for Heroes will arise. The greater the injuries, the more healing will be necessary. Each stage introduces its own disorder. During the response phase, some individuals may be marginalized and replaced by those who align more closely with management’s perspective. The technical team will execute the decisions with the help of external companies. However, there is no clear understanding of the underlying logic, leading to hesitation and indecision about the strategy. The post-crisis phase of data recovery becomes crucial if it is found that some information has been irreversibly lost. Heroes will embark on a relentless search for THE solution, striving to salvage the situation without considering the political implications.
Another complication that could exacerbate the situation is the ongoing investigation. If it turns out that the attack came from inside, this would trigger an atmosphere of distrust, secrecy, and suspicion.
Communication with customers and subcontractors will also face delays. Due to contradictory reports, there persists a cloud of uncertainty regarding the company’s trustworthiness.
Post-mortem examinations are often designed to protect a company’s image, specifically by hiding specific blunders. While this may initially seem like a deceptive tactic, it can actually enhance the company’s image of resilience. The company chooses not to disclose details of the incident, either internally or externally, in an effort to maintain its dignity.
Our heroes will find it challenging to return to normal. The human resources department will follow established procedures without acknowledging the extraordinary circumstances or the dedication displayed by some, having observed these events from a distance.
Since there is a desire to quickly move on from the incident, our heroes find themselves in a very targeted confrontation with human resources. Dismissive comments include: ‘OK, you’ve done a good job. Thank you! Here’s an extra reward to wrap things up. “Let’s get back to work.”
This response fails to adequately address the situation. Disheartened, the hero reflects on the sacrifices made for such a disappointing outcome.
The fall of the Heroes!
THINGS TO REMEMBER
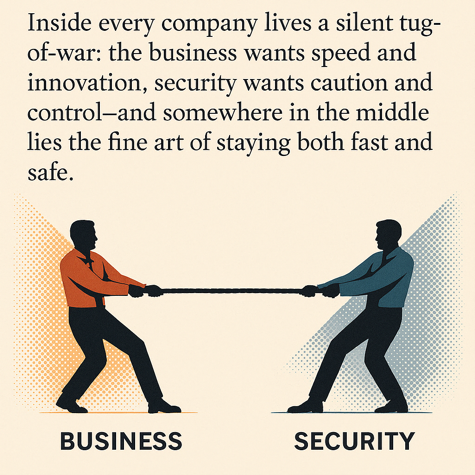
Inside every company lives a silent tug-of-war: the business wants speed and innovation, security wants caution and control — and somewhere in the middle lies the fine art of staying both fast and safe.
Stay tuned for the next episode.
And don’t forget: “Cyberattacks are like glitter — once they’re in your system, they’re everywhere, and good luck getting rid of them!”
About the Author
Didier Annet is an Operational & Data Resilience Specialist and a Certified Professional Coach dedicated to empowering individuals and teams to navigate the complexities of an ever-changing digital landscape.
Find him on LinkedIn: Didier Annet
Learn more in his book:
📖 Guide de survie aux cyberattaques en entreprise et à leurs conséquences psychologiques: Que fait-on des Héros ? (French Edition) – Available on Amazon
Coming soon: The English version – “What Happens to Heroes”